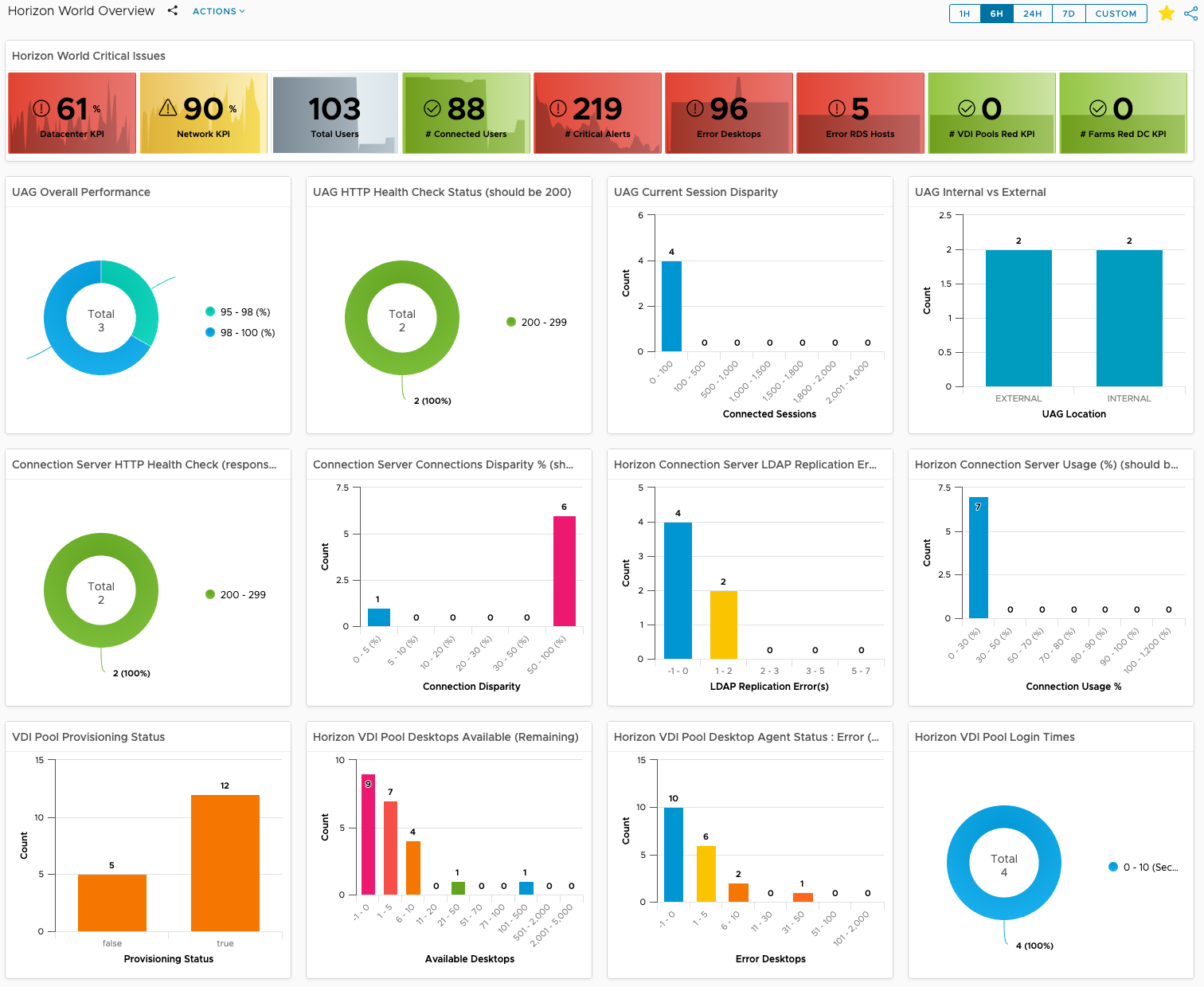
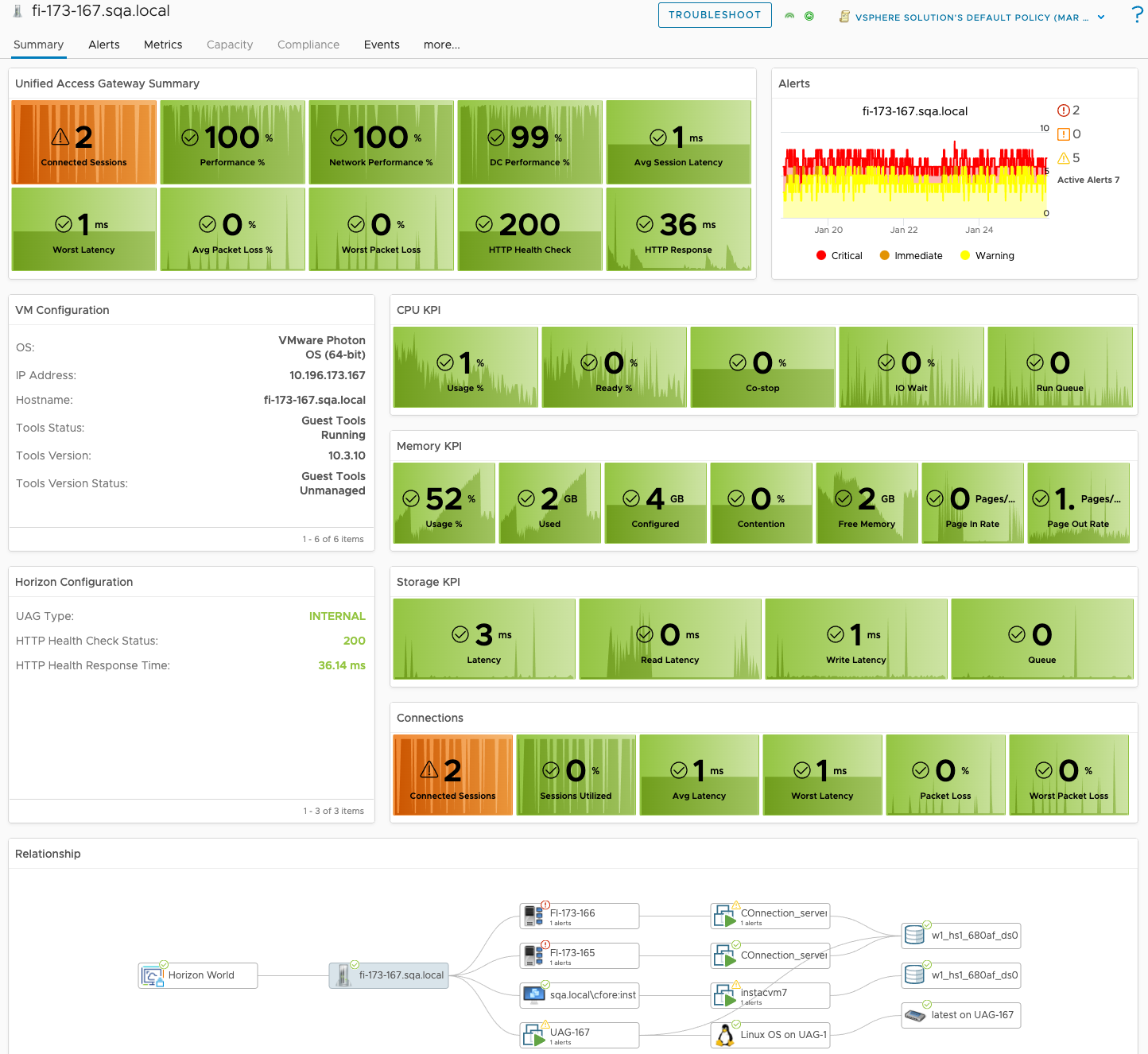
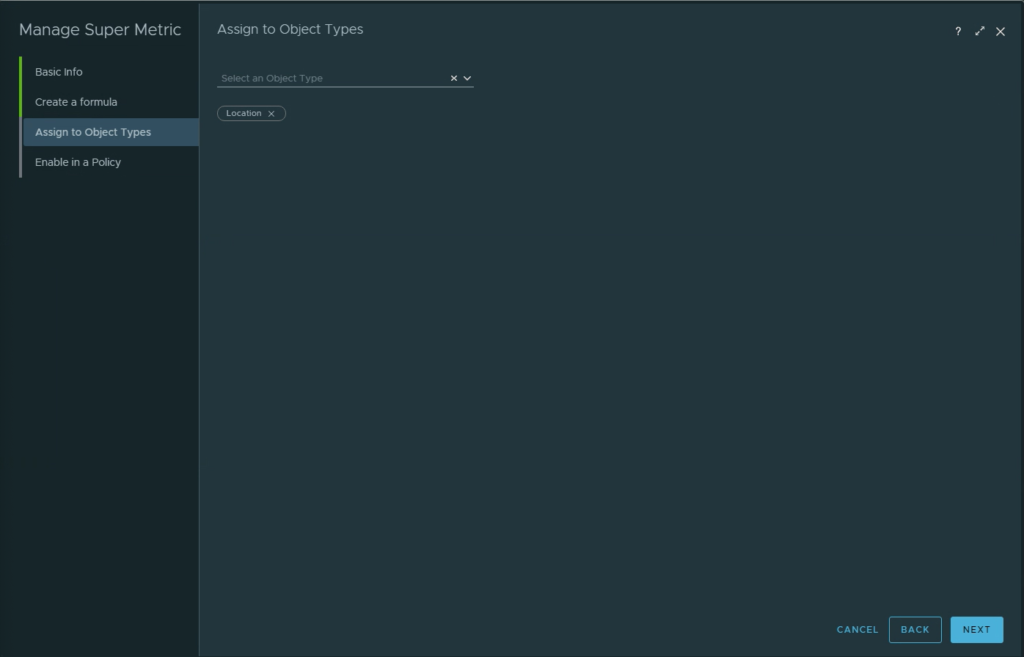
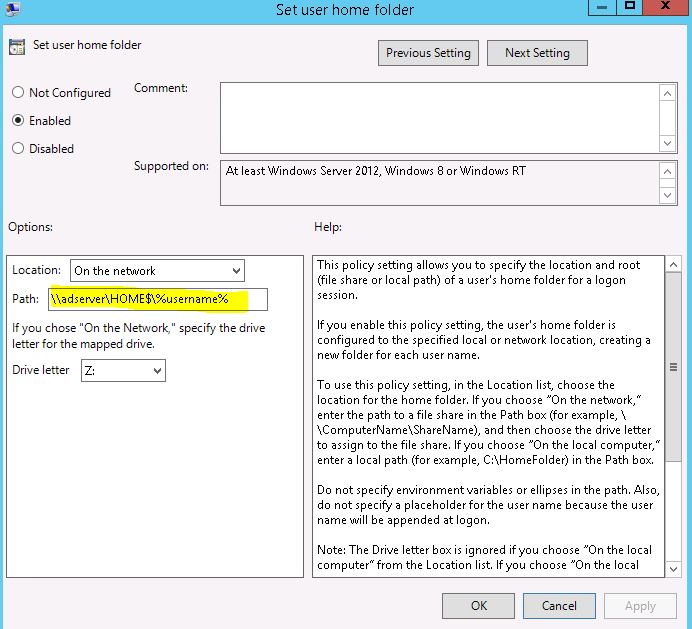
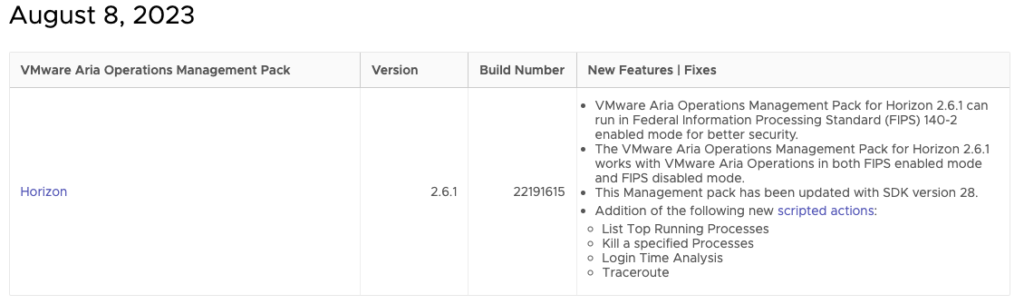
As of August 8th, 2023, the Management Pack for Horizon 2.6.1 is now available. While this is considered a minor release in terms of net new features from 2.6.0, there have been a number of enhancements to the adapter to improve Horizon supportability for new versions of the Horizon platform as well as new features that allow for scripted actions to be performed on connected Horizon sessions.
Top Feature Enhancements
- Horizon VDI Session In-guest Scripted Actions
- Horizon 2303 and 2306 support
- Federal Information Processing Standards (FIPS) 140-2 enhanced security mode.
- Support for the latest Horizon SDK version 28.
Link to Download: https://marketplace.cloud.vmware.com/services/details/vmware-aria-operations-management-pack-for-vmware-horizon-2-6-1-1?slug=true
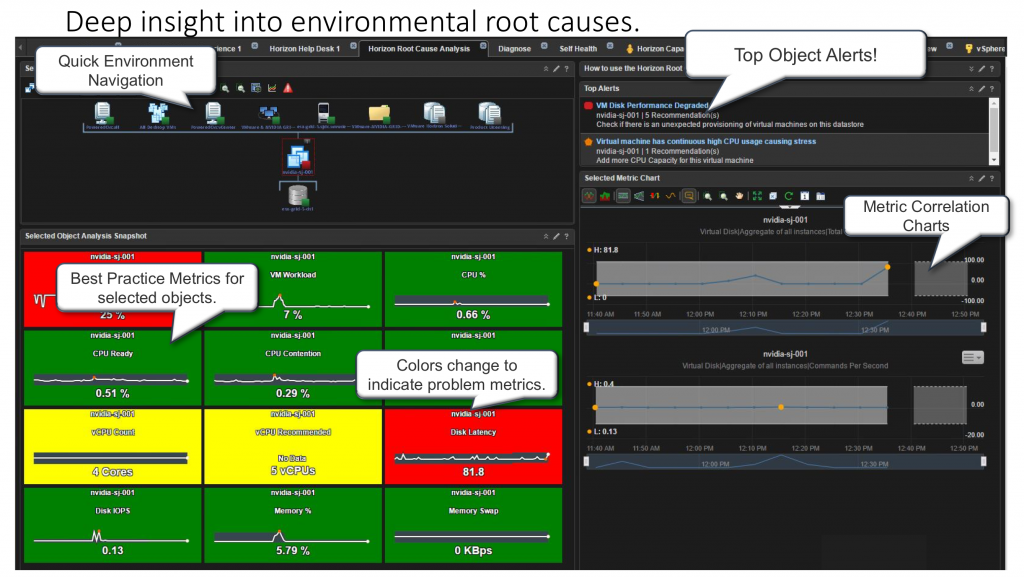
Since scripted actions have been a long-standing customer ask, lets take a look at what actions are now supported when troubleshooting a Horizon User’s VDI session and how to use them.
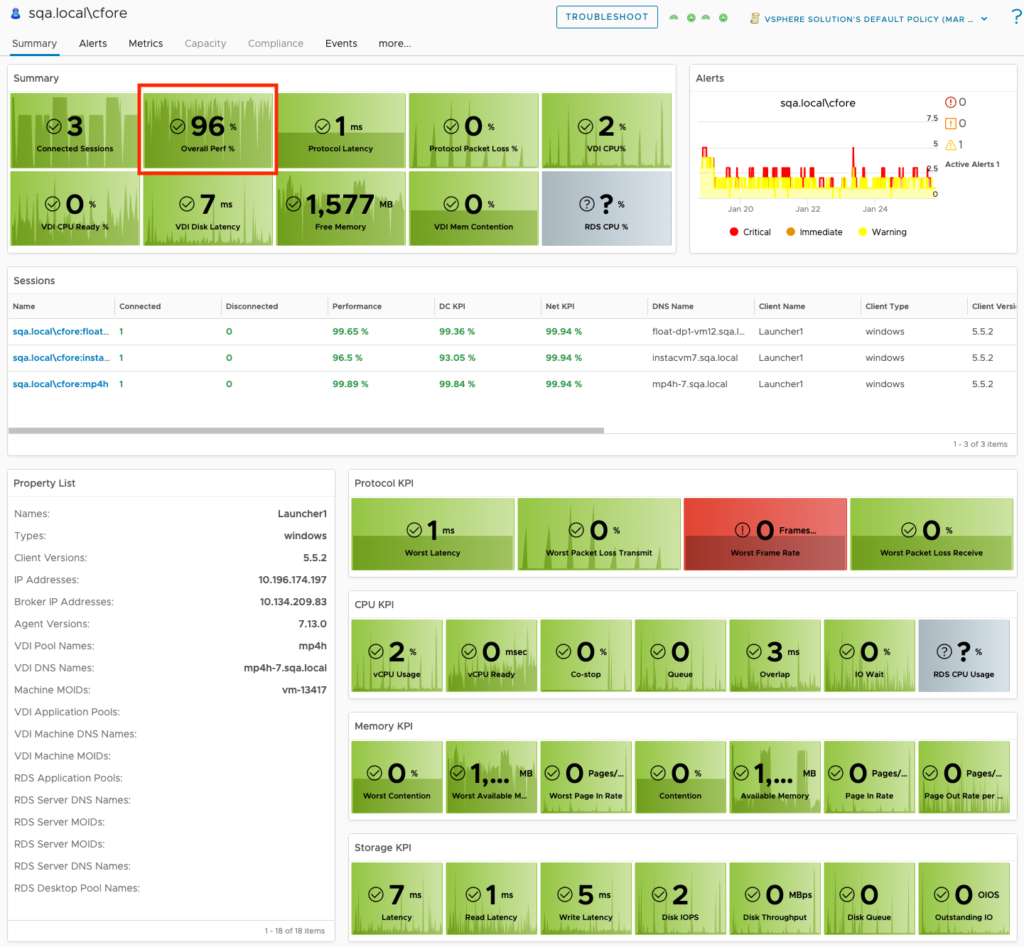
To get started, first we need to find a Horizon User’s VDI Session that we want to troubleshoot. This can be done multiple ways, but the easiest way is to use the search bar and search for the users AD Logon Name. You will see a couple of Horizon object types to select from, one is the User object and the other is the VDI session object(s). The User object is typically the best object to start with if you’re not sure which Session object the User is connected to. If there is only one session object, clicking it directly is the quickest path, but for the sake of this blog I will choose the Horizon User Object.
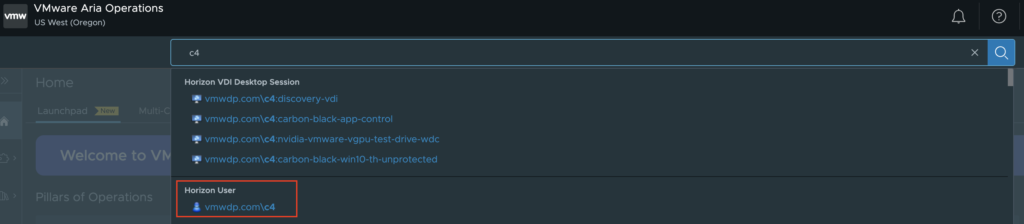
From the User Object Summary Page we will select the VDI session that we want to troubleshoot. **Note: It’s recommended to perform this action on sessions that have Connected Sessions. If the session is in a Disconnected state and the relationship to the desktop no longer exists, then the action will not be able to be performed.
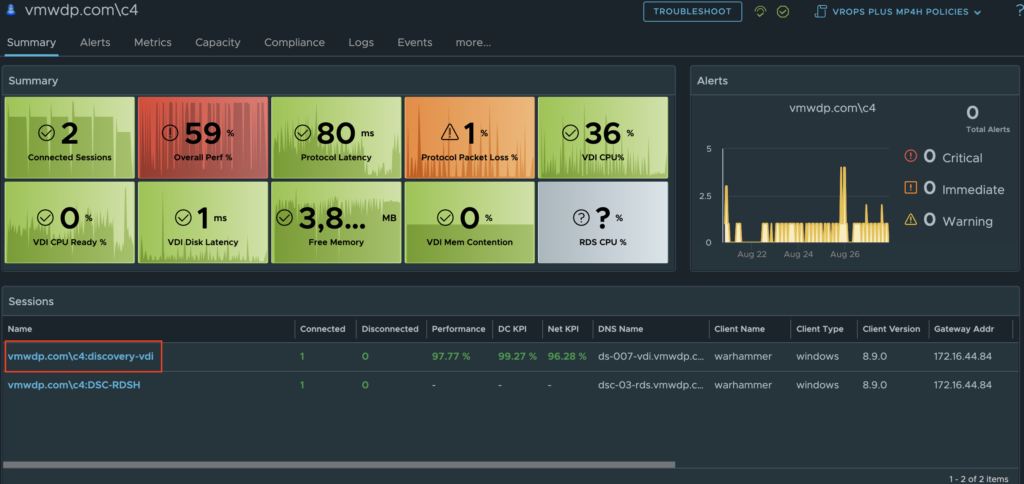
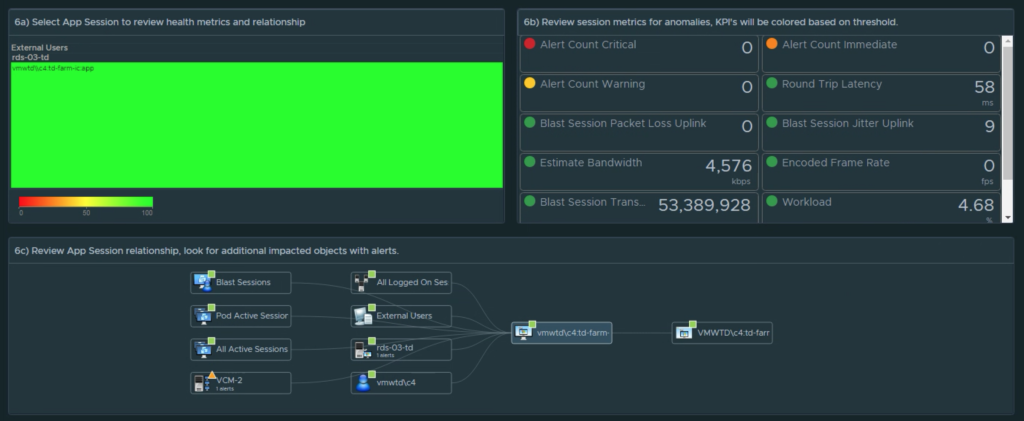
From the User Session Object Summary Page you will notice a new Actions menu option. Click Actions to see the list of available scripted actions that can be performed on the Horizon VDI session.
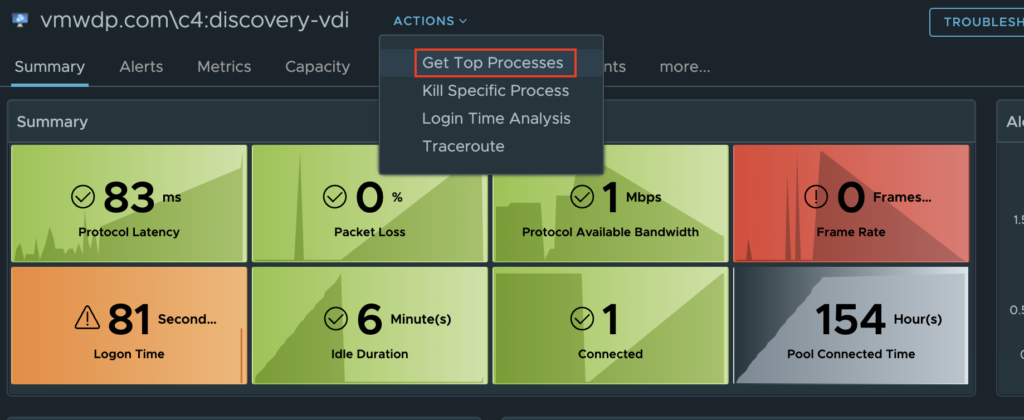
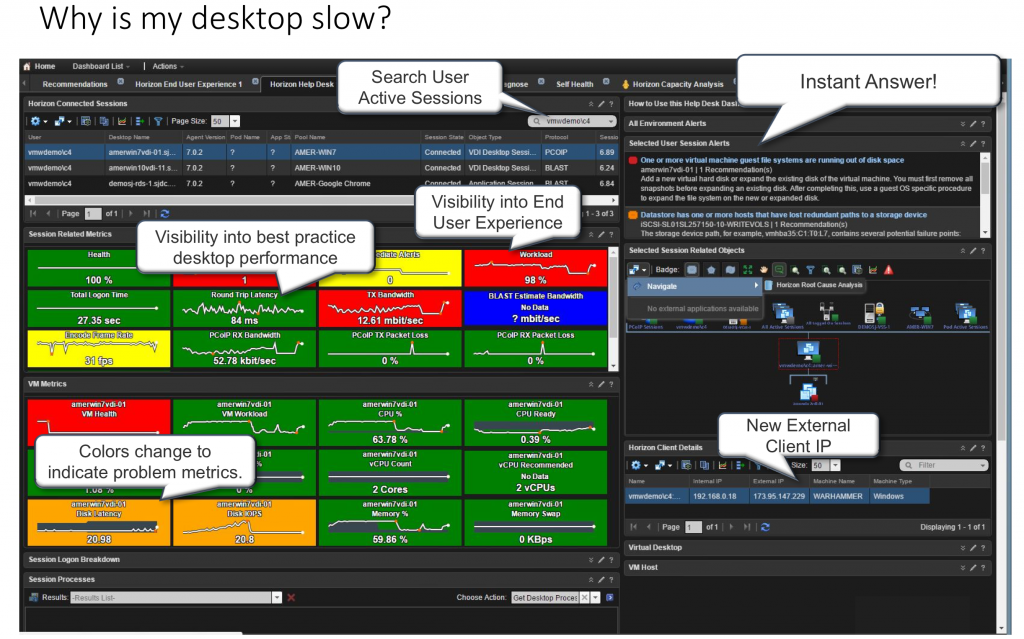
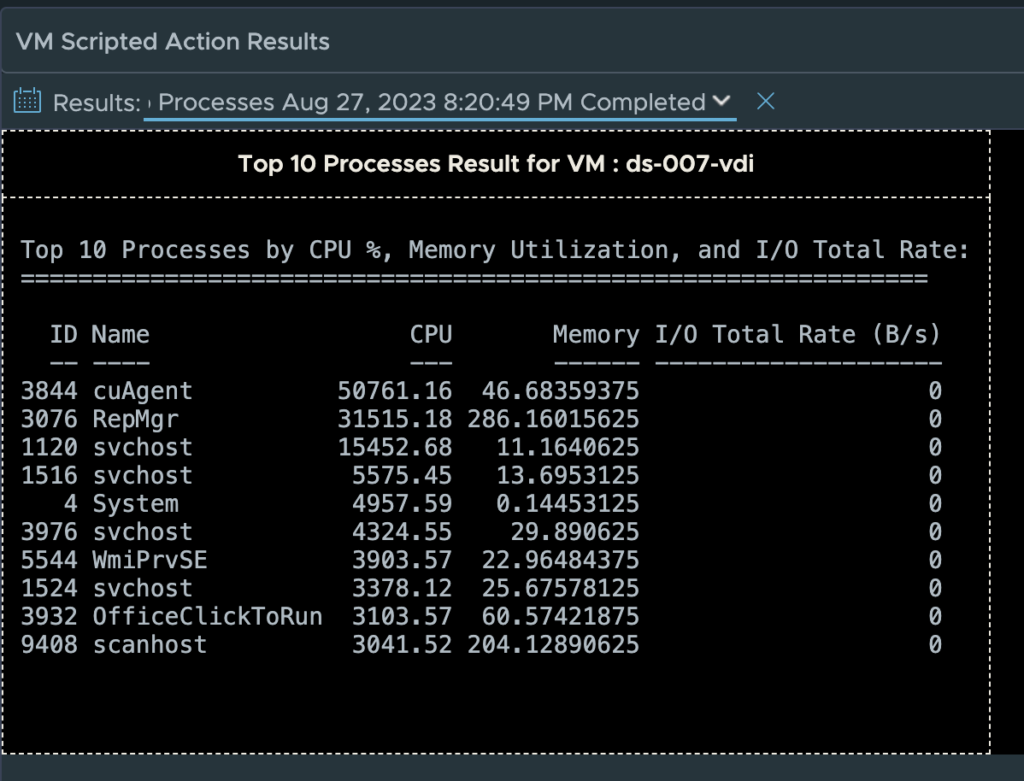
The first available action is “Get Top Processes”, which is meant to provide additional insight as to which processes are consuming the most CPU, Memory, and I/O. This is helpful in scenarios where you see the desktop CPU Usage is > 95% or Available Memory is low < 512MB, and you need to know which process(es) are consuming most of the resources.
Selecting “Get Top Processes” will open a prompt where you will need to provide AD credentials that has admin level access to the Guest OS that can run the desired script.
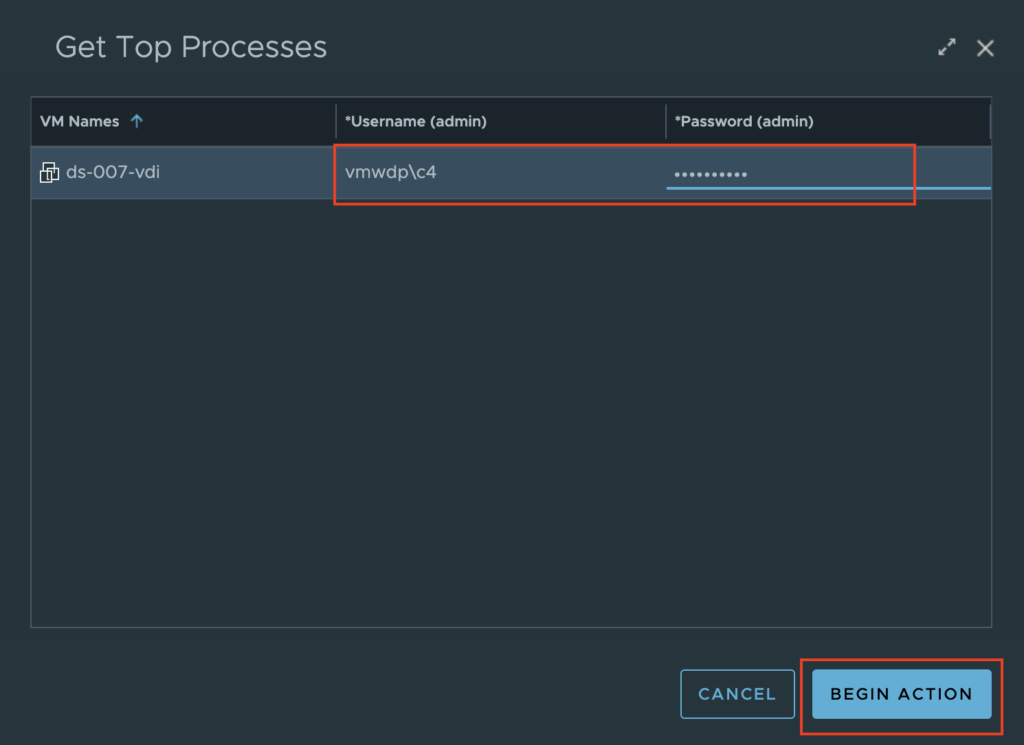
After clicking “Begin Action”, another prompt will appear that lets you know the Task has been created. Clicking on the Task ID will take you a new page that will allow you to watch it’s progress till completion.
Once the task is completed, click the browser back button to return the Horizon Session Summary Page. Scroll down until you see the “VM scripted Actions” widget. Click the “Results:” down arrow and select “Get Top Processes…” from the list.
This is will display the results of the Get Top Processes script if the proper credentials were provided. Otherwise, you may see an error stating the action did not have the appropriate credentials.
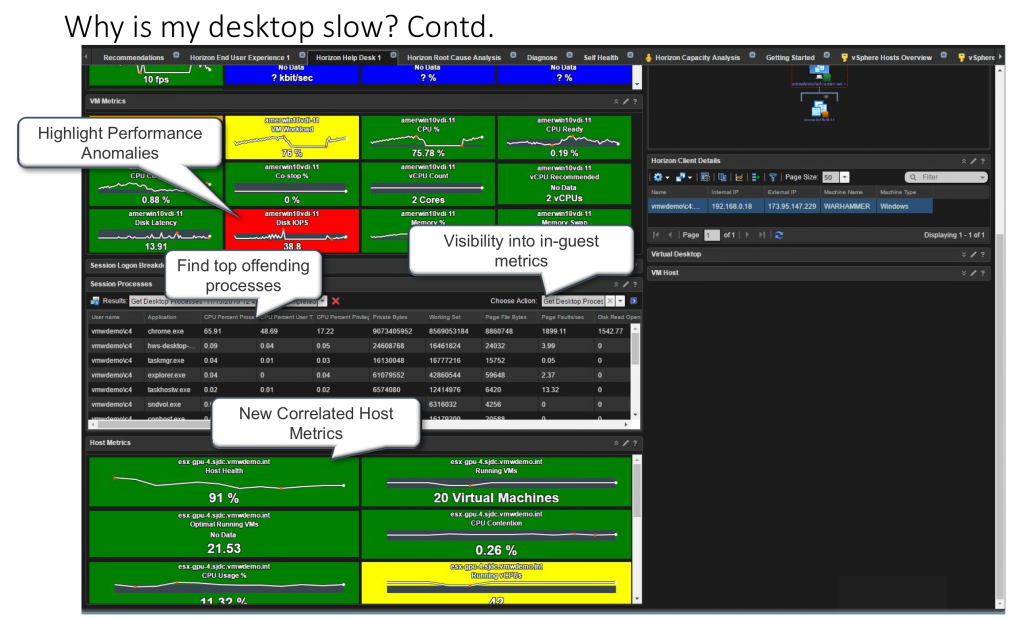
After reviewing the results of the “Get Top Processes” widget, you may decide that you need to terminate a process that is causing performance issues for the user. This is the purpose of the “Kill Specific Process” scripted action.
Just like “Get Top Processes” workflow, select the “Kill Specific Process” action from the “Action” menu. A prompt will appear asking you for the Process ID that you want to terminate and admin credentials that have Guest OS level rights to run the script.
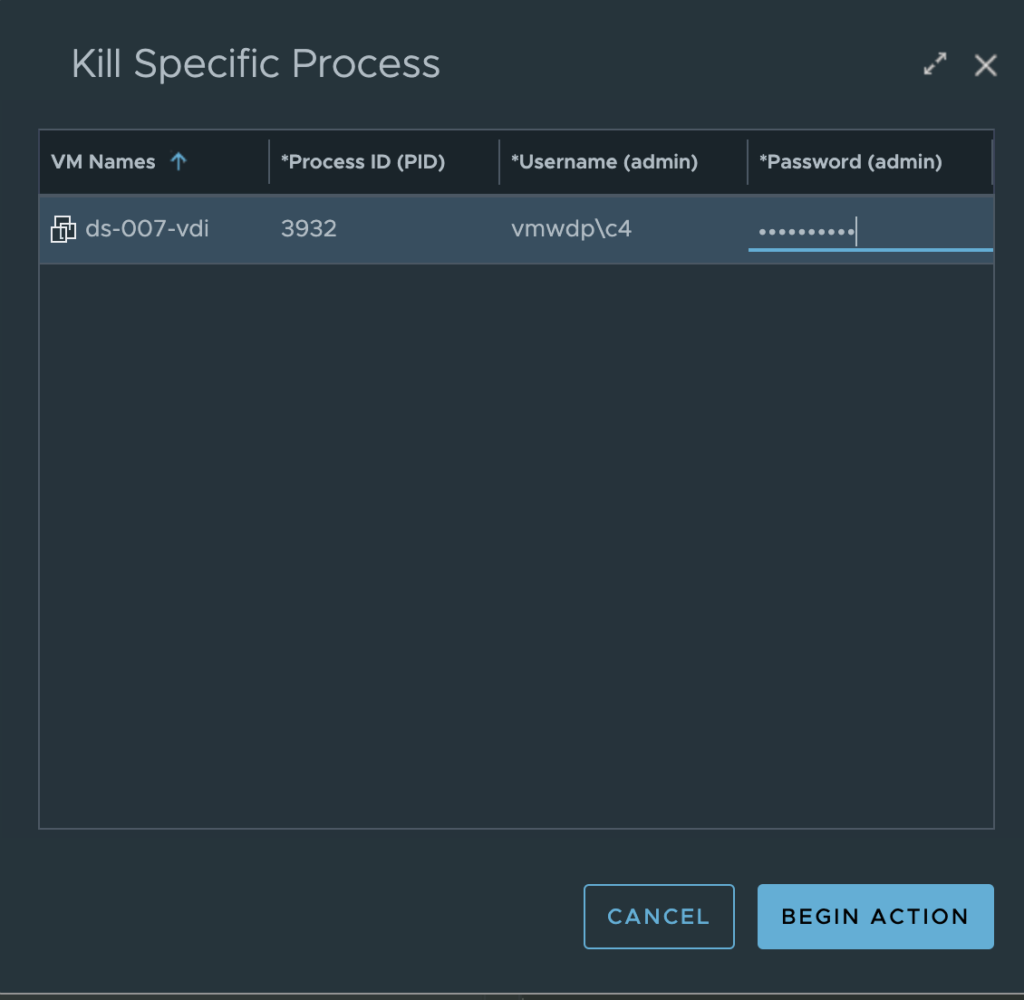
Clicking “Begin Action” will provide you a prompt with the Task ID and link to review the progress of the script execution. Once the action shows “completed”, click the back arrow to return to the VDI Session summary page. Scroll to the “VM Scripted Actions” widget, click the “Results:” down arrow and select the “Kill Specific Process” result to see the action was successful.
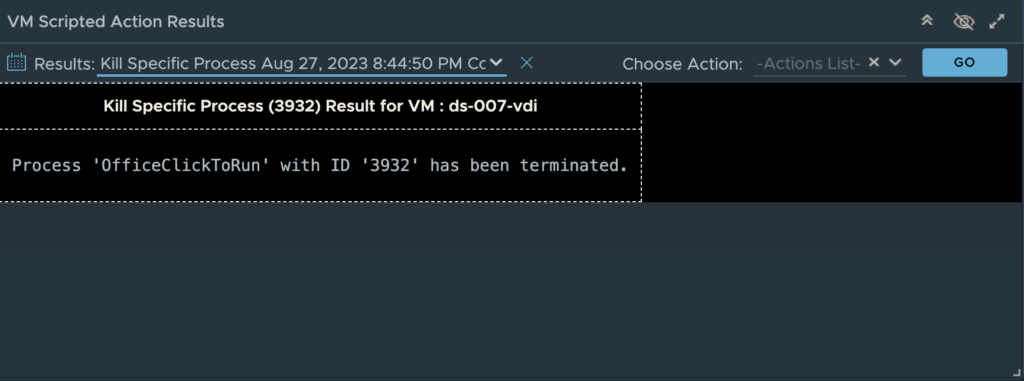
Since the workflow to execute and monitor the actions are basically the same, I will just focus on the purpose and expected outcome of the remaining two actions.
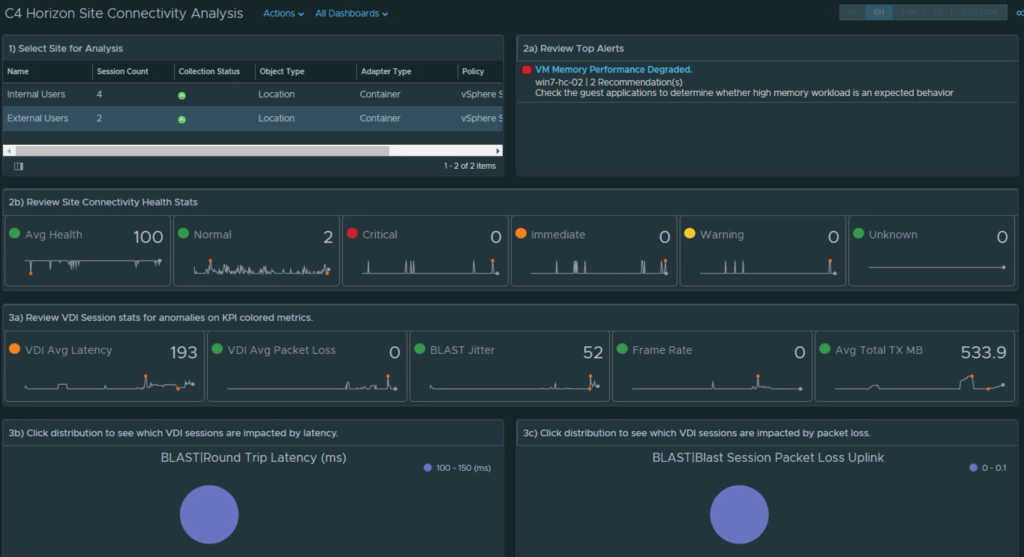
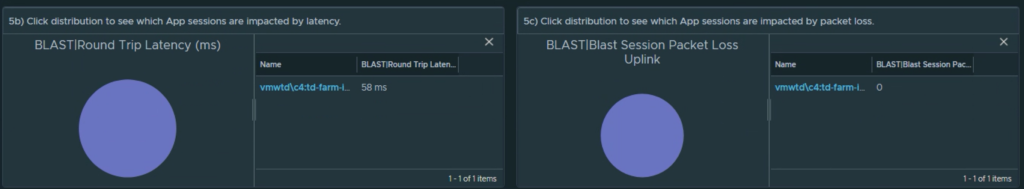
From the beginning of the Management Pack for Horizon we have supported the ability to show and display excessive login times by session, by user, and by which VDI pools have the longest login times.
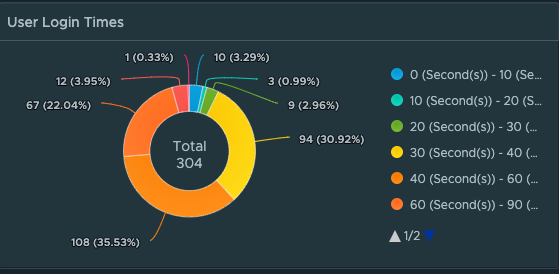
However, to get a full breakdown of every step of the logon process and what factors/events are contributing to the login process requires in-guest scripting to evaluate the timing of all of the logon events. While a portion of the logon process is Horizon brokering, most of the login sequence is purely based on Windows events and services such as Group Policy processing, User Profile loading, Appx file associations and packages, Logon Tasks, App Volumes, and Dynamic Environment Manager (DEM).
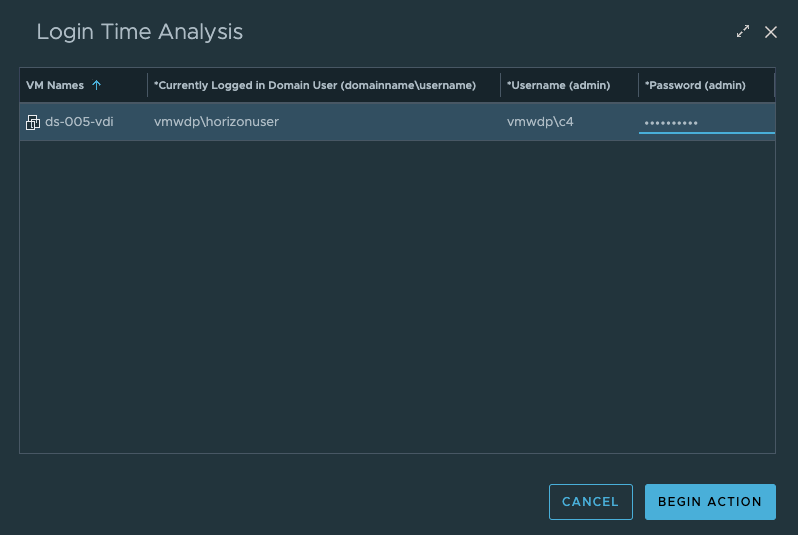
With MP4H 2.6.1, we now provide a detailed Logon Time Analysis scripted action to perform the necessary event analysis and provide a detailed report that shows the breakdown of the logon events and their processing time.
To execute the script properly, you will need to provide the domain\username of the logged in user who you are running the analysis for, as well as the admin credentials that are required to execute the script within the guest OS.
The output can vary depending on which services you are using in your environment and the number of policies and tasks that are being executed. Since the output is long I split it across two images:
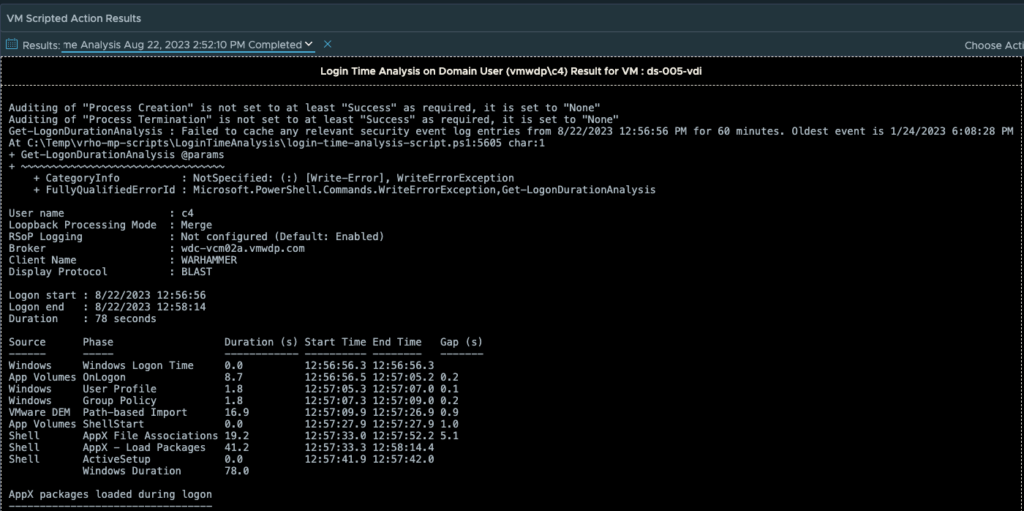
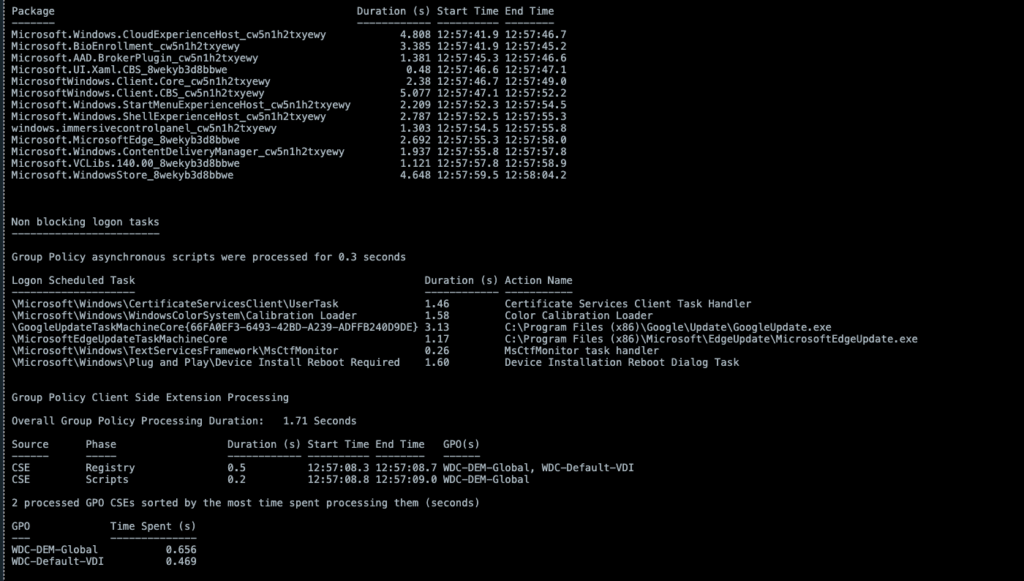
**Note that the total Logon time in the output of the script will be slightly less than the time shown on the Users Session object. This is due to the script only having the rights to view what events are happening at the Windows Guest OS level. Any Horizon events such as brokering are outside of the scope of the scripted action.
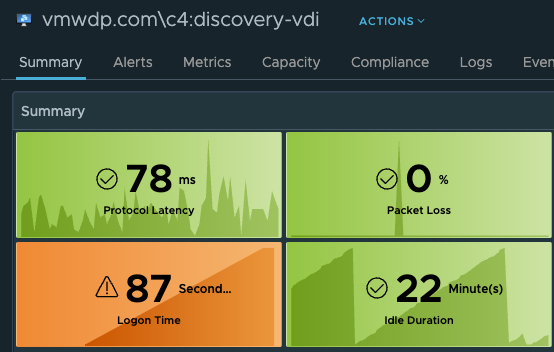
In this specific output of the script, the “Duration” of the login was 78 seconds. However, the User’s VDI Session is showing a total Logon Time of 87 seconds. This is expected behavior given how the two methods of calculating the logon time are very different.
Lastly we have added the option to perform a “Traceroute” from the users desktop to any network target or route that you are trying to troubleshoot performance to. By default the IP Address of the Horizon Client will be populated, but this can be changed to another IP address that is more relevant for a given network troubleshooting scenario.
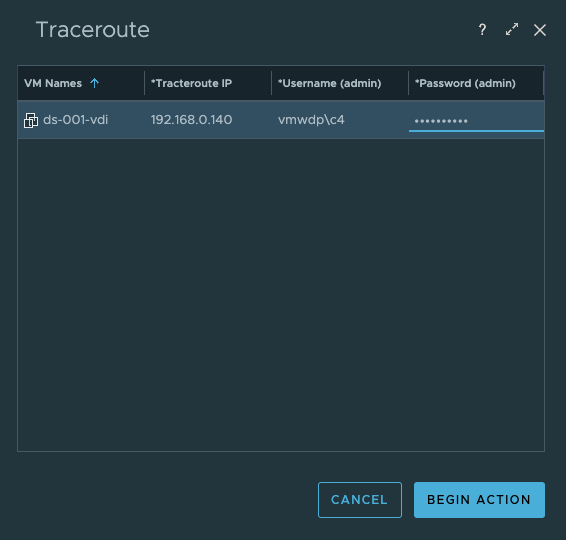
This action is helpful in determining if there are any network communication or performance issues along the route that requires troubleshooting.
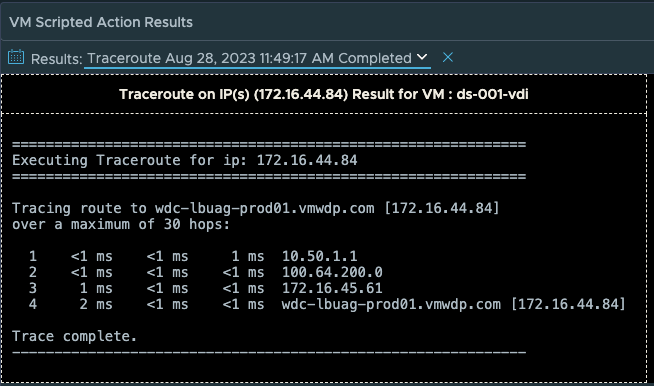
In conclusion, while MP4H 2.6.1 is only a minor release in terms overall features added, we have added some very important functionality to improve how our customers can gain additional insight into performance issues within the Guest OS, take corrective action if needed, provide a detailed login analysis of issues impacting the user’s login experience, as well as providing the ability to do additional network troubleshooting from the User’s desktop.
For the next release, we hope to bring even more valuable features to enhance our customers ability to provide insight and analysis of their Horizon environments and Users. So stay tuned…